Our latest roundup of Mac accessories includes ways to protect your computer, ways to protect your desk, and new ways to get great sound out of your Mac. Amped Wireless The $90 ACA1 is a long. You can use the same subscription username and password to activate your software on either Windows or Mac platforms. Support & Adoption Services.
Please contact us with any additions or amendments to this list, thank you.
AccessData
Forensic Toolkit
https://accessdata.com/products-services/forensic-toolkit-ftk
Forensic Toolkit (FTK) is a database-driven software which performs a wide variety of functions including forensic imaging, registry analysis, decryption of files and password cracking. Its data visualisation options include timeline screenshots formatted for inclusion in case reports, and graphical representations of between-domain communications. FTK can also analyse flesh tones, shapes and orientation for explicit image detection, and analyse suspect binaries without requiring a full malware team.
ADF
Triage-G2
www.adfsolutions.com/products/triage-g2
Triage-G2 is aimed at military and intelligence agents, and can be used to set up customised scans, including the creation of search profiles and SearchPaks. The software is deployed using a small USB drive that can be prepared beforehand or in the field. Preconfigured search profiles make it easy for non-technical operators to use. Triage-G2 supports multiple software platforms including Windows, Mac and Linux. It also includes a stealth mode for investigating live computers.
Triage-Examiner
www.adfsolutions.com/products/triage-examiner
Triage-Examiner provides a solution for forensic examiners and trained investigators. It includes many of the same features as Triage-G2, including the ability to scan SD cards and external digital media, and the creation of SearchPaks. Using ADF’s ActivitySensor, it scans a suspect drive and divides files into four categories: high value, preferred location, allocated and deleted. Collected data can be viewed immediately or stored for later analysis.
Triage-Responder
www.adfsolutions.com/products/triage-responder
Recommended for general investigators and border agents, Triage-Responder is available on a USB dongle and can run scans on both live and dead computers. It is aimed at less experienced users and as such is set up with preconfigured search profiles for ease of use. Digital evidence can be viewed immediately on suspect computers running on Windows, Mac or Linux, and reports are exported in HTML format.
Cellebrite
UFED
www.cellebrite.com/mobile-forensics
Cellebrite’s Universal Forensic Extraction Device (UFED) allows for extraction, analysis and reporting of data from mobile phones. It supports a wide range of devices and operating systems, including iOS, Android, RIM, portable GPS devices and replica devices with Chinese chipsets. UFED bypasses pattern locks and PINs on Android devices, decodes BBM data and other communications made via Blackberry handsets, and obtains both existing and deleted data including passwords, call history, text messages and location information.
Compelson
MOBILedit Forensic Express
https://www.mobiledit.com/forensic-express
MOBILedit Forensic Express is a phone and cloud extractor, data analyzer and report generator. Using both physical and logical data acquisition methods, MOBILedit includes advanced application analysis, deleted data recovery, live updates, a wide range of supported phones including most feature phones, fine-tuned reports, concurrent phone processing, and an easy-to-use user interface. With the password and PIN breaker you can gain access to locked ADB or iTunes backups with GPU acceleration and multi-threaded operations for maximum speed.
Digital Assembly
Adroit Photo Forensics
digital-assembly.com/products/adroit-photo-forensics/
Adroit image carving software allows investigators to recover images from hard drives, drive images and external memory devices. The batch processing option allows investigators to analyse multiple cases simultaneously, and case details can be automatically generated based on preselected evidence. Images can be carved from several areas including file system, unallocated space and fragmented files. MD5 or SHA1/SHA256 hashes can be generated from the recovered photos, which can then be exported into FTK.
DiskTuna
JPEG Recovery LAB
www.disktuna.com/jpeg-recovery-lab-digital-photo-recovery/
JPEG Recovery LAB is an advanced file carver capable of recovering fragmented files (photo and video) from memory cards. Currently supported file formats are JPEG, CR2 (Canon RAW), NEF (Nikon RAW) and MP4, MOV, AVI, MPEG-2 video.
Guidance Software
EnCase Forensic
www.guidancesoftware.com/products/Pages/encase-forensic/overview.aspx
EnCase software supports data acquisition from several operating systems including iOS, Windows for PC, Android, RIM, Windows Mobile and SIM cards. The Evidence Processor allows users to search across multiple devices simultaneously, create templates based on previous cases, and analyse data origins, user activity and timelines. Prioritised processing allows for subsets of evidence to be processed while the remainder is paused or processed in the background. Other EnCase solutions include Enterprise for remote investigations, and Portable, which can be installed on a USB device.
Magnet Forensics
Internet Evidence Finder
www.magnetforensics.com/software/internet-evidence-finder/
Internet Evidence Finder (IEF) is available as either a Standard or Advanced package. The Standard package covers Windows and Mac devices, and performs data carving from social networking sites, instant messenger conversations, cloud-based storage systems, file sharing apps and several other locations. The Advanced version includes all of the same features, with added support for carving data from iOS and Android applications.
MSAB
XRY (extracting & decoding)
https://www.msab.com/products/xry/
XRY mobile forensic tools enable the extraction and decoding of data from mobile devices and apps, including iOS and Android smart phones, cloud services, “burner” feature phones and clone phones, drones, GPS devices, IoT devices and more. Unlike some mobile forensic tools, which were originally designed for other purposes, XRY was designed from its inception to be forensically sound. The XRY file format keeps evidence secure and accounted for at all times, with a full audit trail and protection of the evidence from initial extraction through analysis to reporting and presentation in court or elsewhere. XRY is offered on a selection of open and turnkey hardware platforms, with options for office and field use.
XAMN (analyzing & reporting)
https://www.msab.com/products/xamn/
XAMN enables investigators and analysts to turn mobile device data into vital insights — quickly. XAMN is a suite of analysis tools that enables you to search, filter and visualize huge volumes of mobile forensic data in order to find key pieces of evidence and intelligence. View data and filter by geo-location, timeline, chat conversation and link analysis. XAMN also makes it easy to report and present your findings.
XEC (managing assets)
https://www.msab.com/products/xec/
XEC helps organizations improve the efficiency, speed, visibility and control of their investigative and mobile forensic operations. With XEC, managers can streamline processes and enforce policies, manage and update mobile forensic assets from a central control point, distribute data seamlessly across networks, track key goals, and more.
Nuix

Nuix Investigator Workstation
www.nuix.com/nuix-workstation-investigator
Workstation allows investigators to triage, process and analyse data sets, as well as automatically detecting key items such as contact details, social security data and credit card numbers. It supports a variety of data sources including computer hard drives, smartphones, memory cards, email accounts and cloud-based storage systems. Its pre-filter option examines email and locally stored documents, bringing the most critical information to the forefront for quick examination.
Nuix Investigator Lab
www.nuix.com/Investigator-Lab
Nuix Lab provides a software solution for groups of investigators who are working on the same case. It allows up to five users to collaborate remotely on an investigation and includes several options for portable forensic analysis. Extraction of data from several sources at one time, including forensic images, Microsoft SharePoint, email services and mobile file systems is also available. For smaller groups of investigators, Nuix Investigator Reviewer provides similar capabilities with fewer licenses.
Amped Mac Software Reviews
Oxygen Forensics
Oxygen Forensic Suite
www.oxygen-forensic.com/en/features/
Oxygen Forensic Suite comes in Standard and Analyst packages, and includes a SQLite Viewer which allows exploration of database files, and automated rooting of Android devices. Web connections can be analysed and geographical coordinates can be viewed in Google Earth. The Analyst package provides several more options, including the possibility of aggregating contacts from multiple sources, dictionaries that show all the words that have been entered into a device, and a social graph showing connections between individuals and groups of people. There is also specific support provided for replica devices, particularly those popular in the Asian mobile market.
Paraben
Device Seizure
www.paraben.com/device-seizure.html
An extraction and analysis system for mobile forensics, Device Seizure allows logical extraction of user data including passwords, call logs, SMS and contacts. Physical acquisitions are also possible for many devices, including Android and GPS systems. GPS coordinates from navigation devices and mobile phones can be viewed in Google Earth for ease of use. Paraben also provide a SIM Card Seizure option for investigators who only want to acquire data from SIMs.
P2 Commander
www.paraben.com/p2-commander.html
P2 Commander works across several areas of forensic investigation, including email analysis, with the ability to recover deleted messages; chat log and internet file analysis to piece together conversations and browsing history; and registry analysis with Data Triage, which automatically parses user information from system files to save time during investigations. The specialised pornography detection algorithms can determine whether, and where, illicit images are stored.
Amped Mac Software
Email/Chat Examiner
www.paraben.com/email-examiner.html
Paraben’s Email and Chat Examiners allow users to examine hundreds of different formats, including Outlook, Thunderbird, Windows Mail, ICQ, and Skype. Email Examiner analyses headers, bodies and attachments, and can recover deleted items. Both products allow comprehensive searching and can be converted to different formats or exported for review.
Amped Mac Software Download
Sanderson Forensics
Reconnoitre
sandersonforensics.com/forum/content.php?168-Reconnoitre
Reconnoitre parses data from forensic images, including RAW, dd and EnCase, and displays the data within the context of the investigator’s file system. It identifies which parts of a file came from different VSCs, shows alterations and deletions, and provides the history of a file across VSCs. Maps are available for any pictures containing GPS data, and users can sort outputs to show pictures taken within a specified distance of any given picture.
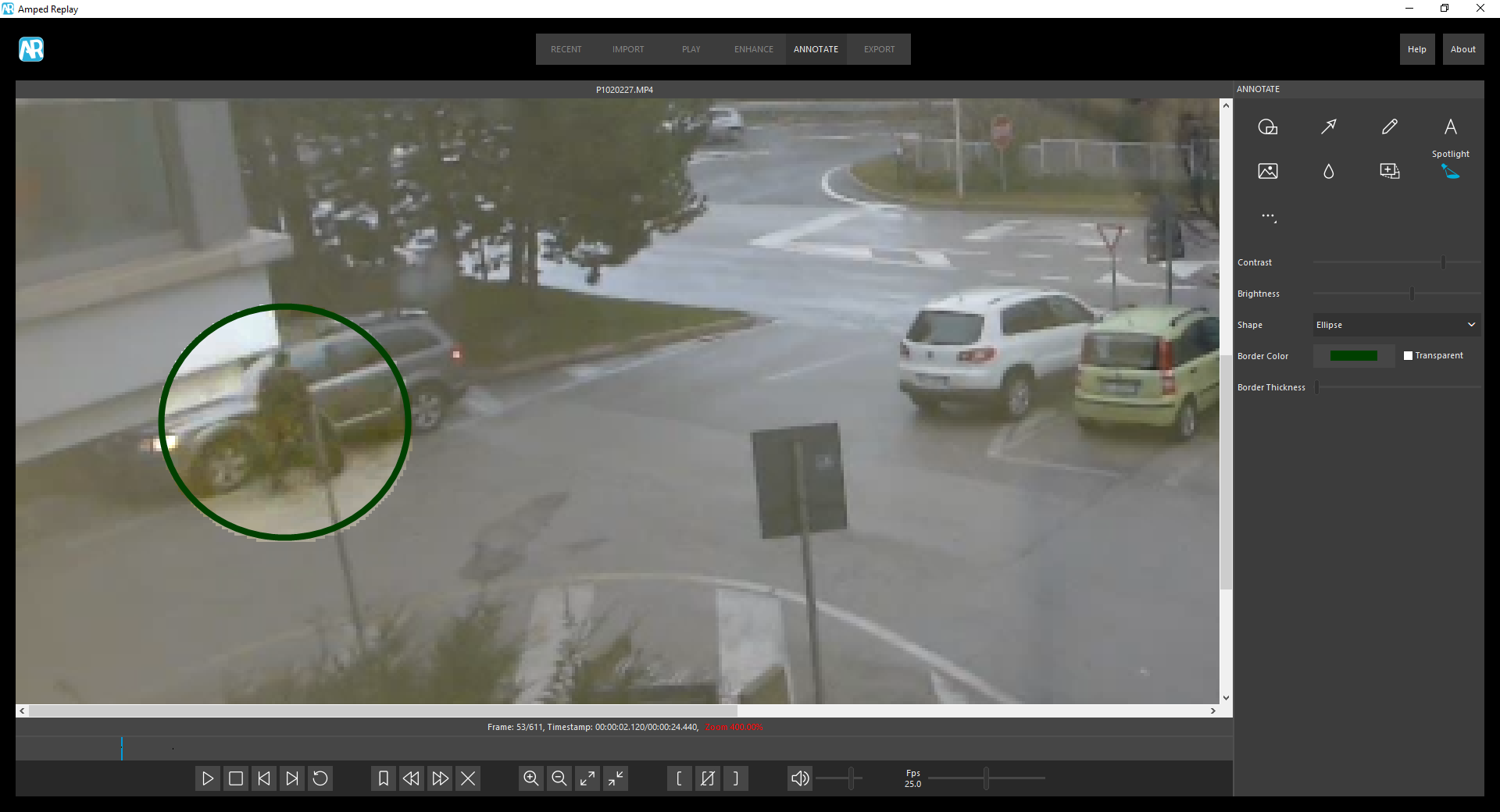
SkypeAlyzer
sandersonforensics.com/forum/content.php?116-SkypeAlyzer
SkypeAlyzer allows investigators to analyse Skype profiles, contacts, voicemails and messages via both .dbb and main.db Skype files. Timelines showing details of calls, chats and file transfers can be generated and extracted as HTML reports. It is also possible to recover deleted Skype records from an image file, or a physical or logical disk.
Sherpa Software
Discovery Attender
www.sherpasoftware.com/microsoft-exchange-products/discovery-attender.shtml
Discovery Attender automates the collection of stored information across Windows platforms. Features include identification of payment card industry and personally identifiable information in files and email; extraction of messages and attachments from Microsoft Exchange Mailboxes, online archives and public folders; and several keyword options including proximity, multi-word phrases and Boolean with wildcards. Results can also be de-duplicated based on custom values including MD5 hash.
Image and Video Analysis
Amped Mac Software Update
Amped Software
Amped FIVE
ampedsoftware.com/five
Amped FIVE provides tools to analyze, restore, enhance, and certify digital image and video evidence. It allows investigators to better see blurry license plates or dark faces, as well as images taken in fog or sandstorms. This technology also enables users to stabilize a full motion video surveillance feed in hostile territories or analyze fingerprints and measurements in the environment, such as the height of a person or the length of a car. Amped FIVE also generates a technical report that validates the integrity of the evidence in order to be admissible in court.
Amped Authenticate
ampedsoftware.com/authenticate
Amped Authenticate is a software package for forensic image authentication and tamper detection on digital photos. It provides a suite of different tools to determine whether an image is an unaltered original, an original generated by a specific device, or the result of a manipulation with a photo editing software and thus may not be admissible as evidence.